

Michael Saylor faced obstacles before he successfully added Bitcoin to MicroStrategy's balance sheet in 2020.
Speaking at the 2024 Abundance360 Summit this week, Saylor revealed how he offered to buy out MicroStrategy shareholders in a Dutch action when they moved to first acquire $250 million worth of Bitcoin.
The comments come after Saylor and his company announced earlier this week that they had purchased approximately 9,245 bitcoins for around $623 million. This latest acquisition brings MicroStrategy's total holdings to about 214,246 BTC.
In a video clip from the conference, Saylor explained how he offered MicroStrategy shareholders the option to tender their shares back to the company as they were buying Bitcoin.
"We announced that we would do a Dutch auction and buy back $250 million of the stock at a premium. The stock was about $121-$122. We offered to buy our shareholders out at $140. We gave 20 days to think about it." Saylor explained.
He said his philosophy was to "buy Bitcoin" and that he was willing to do whatever it took to accumulate more. At the time, the Bitcoin was price was roughly $11,000, down from all-time highs at $20,000 set in 2017.
Saylor's aggressiveness in acquiring Bitcoin for MicroStrategy has made the enterprise software company one of the largest corporate holders of Bitcoin. The company currently holds over $13.7 billion worth of BTC, making Bitcoin its primary corporate treasury asset.
MicroStrategy has since financed its bitcoin purchases through debt offerings and equity issuances, even as the bitcoin market has declined, and has made clear he has no plans to sell his stash anytime soon.
The below is an excerpt from a recent edition of Bitcoin Magazine Pro, Bitcoin Magazine's premium markets newsletter. To be among the first to receive these insights and other on-chain bitcoin market analysis straight to your inbox, subscribe now.

As we get closer and closer to the impending Bitcoin halving, the combined pressures of wildly increasing demand and shrinking supply have created an unusual market, turning a historically positive omen into an explosive opportunity for profit.
The Bitcoin ETF approval has changed the face of Bitcoin as we know it. Since the SEC made its fateful decision in January, the resultant developments have caused worldwide upheaval; billions have flown into these new investment opportunities, and regulators in many countries are considering the role of Bitcoin in the financial establishment. Despite some initial setbacks, the market has comfortably hit new all-time highs, and the price has stayed in a very impressive range even despite fluctuations.
Nevertheless, we are in a very unique situation that can impact the market in unpredictable ways. Bitcoin's next halving is set to arrive in April, and this will be the first time in its entire history that the halving will coincide with an all-time high for price. Although there have been a great deal of differences between each of the major halvings, a trend has been generally noticeable: even if there are huge steady gains, it is in the ballpark of a year to 18 months before Bitcoin breaks all records with a true price spike. One year out from the halving in June 2016, Bitcoin had more than doubled; yet a few months later, the growth was closer to 30x.
There is plenty of optimism from substantial industry players, such as Standard Chartered's bold prediction that Bitcoin's value will more than double to $150k before the year is over. However, their analysis of the situation is not mostly based on halving trends but on the rampaging success of the Bitcoin ETF, and that success has also thrown us a curveball. As community discussion has been quick to point out, these major ETF issuers have been pouring billions into bitcoin, buying at astounding rates and amassing some of the world's largest Bitcoin supplies practically overnight. If they collectively purchase more than even the worldwide community, how will they react when the spigot of new coins shuts to a trickle?
In other words, we are headed into a situation where demand is at an all-time high and there is insufficient supply to meet it. Business Insider called the upcoming halving a "momentous event", considering that the ETF had made "permanent changes to Bitcoin's underlying infrastructure." Coinshares echoed these sentiments with the warning of a positive demand shock, as Head of Research James Butterfill claimed that "The launch of multiple spot bitcoin ETFs on January 11 has led to an average daily demand of 4500 bitcoins (trading days only), while only an average of 921 new bitcoin were minted per day." And that's only considering the pre-halving mining rates. The ETF issuers are already relying on secondhand Bitcoin sales to fill up their coffers, and this trend seems certain to increase in the immediate future.
Isn't this a good thing, though? Positive demand shocks, as a rule, are generally associated with jumps in price. Additionally, even though shocks like this in critical commodities like oil can lead to inflation, Bitcoin is not yet an essential component of the entire world economy. It's unlikely that the same drawbacks will apply just yet. In other words, the answer is generally yes, but the situation can still cause alarming trends. For example, the night of March 18 saw a truly bewildering development: coasting at highs around $70k, Bitcoin's value on BitMEX crashed below $9k in the blink of an eye. The price recovered quickly and was, in any event, isolated to this one exchange, but it's still an unprecedented development.
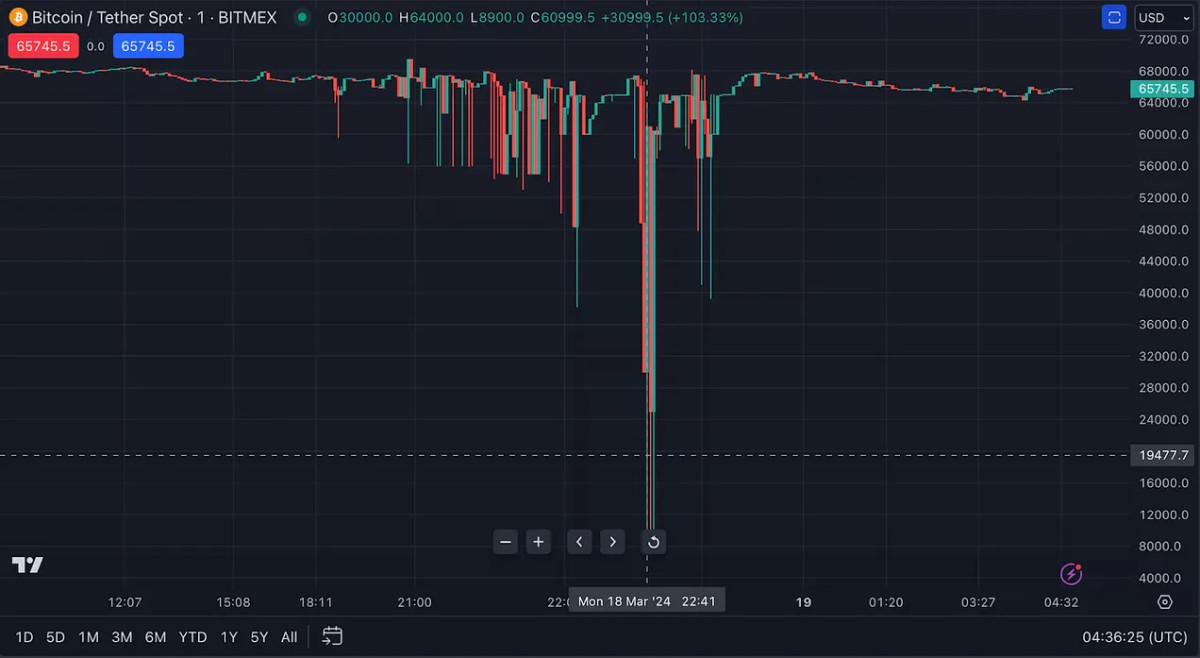
BitMEX announced that the culprit of this negative price spike was a series of large sell orders in the middle of the night, and that they were investigating the activity. Several anonymous whales in particular have emerged as the likely candidates for these sales. We still have no idea who exactly they are or who was buying bitcoins at such a prodigious rate, but it's only an example of how major selloffs can torpedo market confidence. In any event, this one episode is only a particularly sharp example of a general trend; "constant" spot selling as Bitcoin's price receives a bloody nose. The market hit lows of $62k Tuesday afternoon, while it was nearly at $72k on the morning of the previous Friday.
Traders have nevertheless remained totally optimistic that these price dips are nothing more than the "bear trap" associated with the pre-halving environment, and they aren't the only ones. Prominent executives including Binance CEO Richard Teng and Crypto.com CEO Kris Marszalek have endorsed the viewpoint that these kinds of price dips are a perfectly natural and temporary component of a scheduled halving. There is a clearly observable trend of substantial price dips, from 20-40%, in the weeks immediately prior to the most recent halvings. And yet, the price bounced back quickly and completely, and went on to new all-time heights.
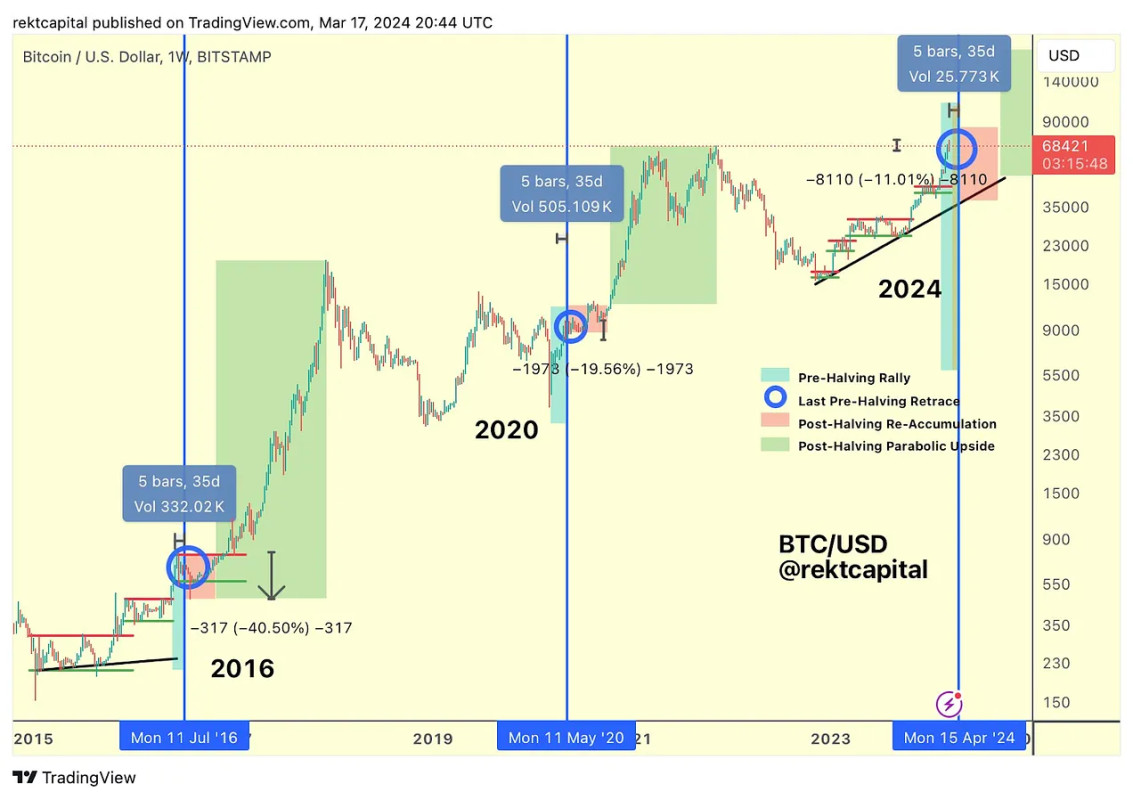
In other words, some of the recent and sudden price dives are fully explainable using data from Bitcoin's history. The relevant questions for us, then, are whether Bitcoin's future will follow the same line. The fact of the matter is that all the available signs point to an optimistic long-term forecast. A positive demand shock caused by ETF acquisitions and the halving may very well make it more difficult for an average consumer to buy bitcoin, but how will that difficulty manifest? Higher prices. Besides, a selling point of the ETF is that plenty of average consumers will use it to seek exposure to bitcoin's profits, rather than direct custody. This alone will encourage ETF issuers to keep their buying pressure high. It's impossible to say how long this market situation will continue or what it will mean for bitcoin's use as an actual currency, but there's nothing in the current situation to suggest that bitcoin won't keep growing.
Is it any wonder, then, that the community is gearing up to welcome the halving with such bated breath? Prominent industry figures are taking great care to prepare "The Biggest Celebration in Bitcoin" with live coverage and meetup events in 7 countries (and counting), and the halving isn't even expected for another month. It's very possible that 2024 will be remembered as the year that Bitcoin truly became enmeshed in the global financial infrastructure, if stunning regulatory victories in January turn to unprecedented growth by December. Really, the major significant concern is whether or not Bitcoin will see diminished usage as a currency when its worth in fiat is so valuable. Nevertheless, the signs from right now seem quite clear: Bitcoin is set to blaze a trail into the future.
This article is featured in Bitcoin Magazine's "The Inscription Issue". Click here to get your Annual Bitcoin Magazine Subscription.
Click here to download a PDF of this article.
Data is the most liquid commodity market in the world. In the smartphone era, unless extreme precautions are taken, everywhere you go, everything you say, and everything you consume is quantifiable among the infinite spectrum of the information goods markets. Information goods, being inherently nonphysical bits of data, can be conceptualized, crafted, produced, or manufactured, disseminated, and consumed exclusively as digital entities. The internet, along with other digital technologies for computation and communication, serves as a comprehensive e-commerce infrastructure, facilitating the entire life cycle of designing, producing, distributing, and consuming a wide array of information goods. The seamless transition of existing information goods from traditional formats to digital formats is easily achievable, not to mention the collection of media formats completely infeasible in the analog world.
A preliminary examination of products within the information goods industry reveals that, while they all exist as pure information products and are uniformly impacted by technological advancements, their respective markets undergo distinct economic transformation processes. These variations in market evolution are inherently tied to differences in product characteristics, production methods, distribution channels, and consumption patterns. Notably, the separation of value creation and revenue processes introduces opportunistic scenarios, potentially leaving established market players with unprofitable customer bases and costly yet diminishing value-creation processes.
Simultaneously, novel organizational architectures may emerge in response to evolving technological conditions, effectively creating and destroying traditional information good markets overnight. The value chains, originally conceived under the assumptions of the traditional information goods economy, undergo radical redesigns as new strategies and tooling materialize in response to the transformative influence of digital production, distribution, and consumption on conventional value propositions for data. For example, mass surveillance was never practical when creating even a single photo meant hours of labor within a specialized photo development room with specific chemical and lightning conditions. Now that there is a camera on every corner, a microphone in every pocket, a ledger entry for every financial transaction, and the means to transmit said data essentially for free across the planet, the market conditions for mass surveillance have unsurprisingly given rise to mass surveillance as a service.
An entirely new industry of "location firms" has grown, with The Markup having demarcated nearly 50 companies selling location data as a service in a 2021 article titled "There's a Multibillion-Dollar Market for Your Phone's Location Data" by Keegan and Ng. One such firm, Near, is self-described as curating "one of the world's largest sources of intelligence on People and Places", having gathered data representing nearly two billion people across 44 countries. According to a Grand View Research report titled "Location Intelligence Market Size And Share Report, 2030", the global location intelligence data market cap was worth an estimated "$16.09 billion in 2022 and is projected to grow at a compound annual growth rate (CAGR) of 15.6% from 2023 to 2030". The market cap of this new information goods industry is mainly "driven by the growing penetration of smart devices and increasing investments in IoT [internet of things] and network services as it facilitates smarter applications and better network connectivity", giving credence to the idea that technological advancement front-runs network growth which front-runs entirely new forms of e-commerce markets. This, of course, was accelerated by the COVID-19 pandemic, in which government policies resulted in "the increased adoption of location intelligence solutions to manage the changing business scenario as it helps businesses to analyze, map, and share data in terms of the location of their customers", under the guise of user and societal health.
Within any information goods market, there are only two possible outcomes for market participants: distributing the acquired data or keeping it for yourself.

In the fall of 2021, China launched the Shanghai Data Exchange (SDE) in an attempt to create a state-owned monopoly on a novel speculative commodities market for data scraped from one of the most digitally surveilled populations on the planet. The SDE offered 20 data products at launch, including customer flight information from China Eastern Airlines, as well as data from telecommunications network operators such as China Unicom, China Telecom, and China Mobile. Notably, one of the first known trades made at the SDE was the Commercial Bank of China purchasing data from the state-owned Shanghai Municipal Electric Power Company under the guise of improving their financial services and product offerings.
Shortly before the founding of this data exchange, Huang Qifan, the former mayor of Chongqing, was quoted saying that "the state should monopolize the rights to regulate data and run data exchanges", while also suggesting that the CCP should be highly selective in setting up data exchanges. "Like stock exchanges, Beijing, Shanghai and Shenzhen can have one, but a general provincial capital city or a municipal city should not have it."
While the current information goods market has led to such innovations such as speculation on the purchasing of troves of user data, the modern data market was started in earnest at the end of the 1970s, exemplified in the formation of Oracle Corporation in 1977, named after the CIA's "Project Oracle", which featured eventual Oracle Corporation co-founders Larry Ellison, Robert Miner, and Ed Oates. The CIA was their first customer, and in 2002, nearly $2.5 billion worth of contracts came from selling software to federal, state, and local governments, accounting for nearly a quarter of their total revenue. Only a few months after September 11, 2001, Ellison penned an op-ed for The New York Times titled "A Single National Security Database" in which the opening paragraph reads "The single greatest step we Americans could take to make life tougher for terrorists would be to ensure that all the information in myriad government databases was copied into a single, comprehensive national security database". Ellison was quoted in Jeffrey Rosen's book The Naked Crowd as saying "The Oracle database is used to keep track of basically everything. The information about your banks, your checking balance, your savings balance, is stored in an Oracle database. Your airline reservation is stored in an Oracle database. What books you bought on Amazon is stored in an Oracle database. Your profile on Yahoo! is stored in an Oracle database". Rosen made note of a discussion with David Carney, a former top-three employee at the CIA, who, after 32 years of service at the agency, left to join Oracle just two months after 9/11 to lead its Information Assurance Center:
"How do you say this without sounding callous?" [Carney] asked. "In some ways, 9/11 made business a bit easier. Previous to 9/11 you pretty much had to hype the threat and the problem." Carney said that the summer before the attacks, leaders in the public and private sectors wouldn't sit still for a briefing. Then his face brightened. "Now they clamor for it!"
This relationship has continued for 20 years, and in November 2022, the CIA awarded its Commercial Cloud Enterprise contract to five American companies -- Amazon Web Services, Microsoft, Google, IBM, and Oracle. While the CIA did not disclose the exact value of the contract, documents released in 2019 suggested it could be "tens of billions" of dollars over the next 15 years. Unfortunately, this is far from the only data market integration of the private sector, government agencies, and the intelligence community, perhaps best exemplified by data broker LexisNexis.
LexisNexis was founded in 1970, and is, as of 2006, the world's largest electronic database for legal and public-records-related information. According to their own website, LexisNexis describes themselves as delivering "a comprehensive suite of solutions to arm government agencies with superior data, technology and analytics to support mission success". LexisNexis consists of nine board members: CEO Haywood Talcove; Dr. Richard Tubb, the longest serving White House physician in U.S. history; Stacia Hylton, former Deputy Director of the U.S. Marshal Service; Brian Stafford, former Director of the U.S. Secret Service; Lee Rivas, CEO for the public sector and health care business units of LexisNexis Risk Solutions; Howard Safir, former NYPD Commissioner and Associate Director of Operations for the U.S. Marshals Service; Floyd Clarke, former Director of the FBI; Henry Udow, Chief Legal Officer and Company Secretary for the RELX Group; and lastly Alan Wade, retired Chief Information Officer for the CIA.
While Wade was still employed by the CIA, he founded Chiliad with Christine Maxwell, sister of Ghislaine Maxwell, and daughter of Robert Maxwell. Christine Maxwell is considered "an early internet pioneer", having founded Magellan in 1993, one of the premier search engines on the internet. After selling Magellan to Excite, she reinvested her substantial windfall into another big data search technology company: the aforementioned Chiliad. According to a 2020 report by OYE.NEWS, Chiliad made use of "on-demand, massively scalable, intelligent mining of structured and unstructured data through the use of natural language search technologies", with the firm's proprietary software being "behind the data search technology used by the FBI's counterterrorism data warehouse".
As recently as November 2023, the Wade-connected LexisNexis was given a $16-million, five-year contract with the U.S. Customs and Border Protection "for access to a powerful suite of surveillance tools", according to available public records, providing access to "social media monitoring, web data such as email addresses and IP address locations, real-time jail booking data, facial recognition services, and cell phone geolocation data analysis tools". Unfortunately, this is far from the only government agency to utilize LexisNexis' data brokerage with the aims of circumnavigating constitutional law and civil liberties in regards to surveillance.
In the fall of 2020, LexisNexis was forced to settle for over $5 million after a class action lawsuit alleged the broker sold Department of Motor Vehicle data to U.S. law firms, who were then free to use it for their own business purposes. "Defendants websites allow the purchase of crash reports by report date, location, or driver name and payment by credit card, prepaid bulk accounts or monthly accounts", the complaint reads. "Purchasers are not required to establish any permissible use provided in the DPPA to obtain access to Plaintiffs' and Class Members' MVRs". In the summer of 2022, a Freedom of Information Act request revealed a $22 million contract between Immigration and Customs Enforcement and LexisNexis. Sejal Zota, a director at Just Futures Law and a practicing attorney working on the lawsuit, made note that LexisNexis makes it possible for ICE to "instantly access sensitive personal data -- all without warrants, subpoenas, any privacy safeguards or any show of reasonableness".
In the aforementioned complaint from 2022, the use of LexisNexis' Accurint product allows "law enforcement officers [to] surveil and track people based on information these officers would not, in many cases, otherwise be able to obtain without a subpoena, court order, or other legal process...enabling a massive surveillance state with files on almost every adult U.S. consumer".
In 2013, it came to the public's attention that the National Security Agency had covertly breached the primary communication links connecting Yahoo and Google data centers worldwide. This information was based on documents published by WikiLeaks, originally obtained from former NSA contractor Edward Snowden, and corroborated by interviews of government officials.
As per a classified report dated January 9, 2013, the NSA transmits millions of records daily from internal Yahoo and Google networks to data repositories at the agency's Fort Meade, Maryland headquarters. In the preceding month, field collectors processed and returned 181,280,466 new records, encompassing "metadata" revealing details about the senders and recipients of emails, along with time stamps, as well as the actual content, including text, audio, and video data.
The primary tool employed by the NSA to exploit these data links is a project named MUSCULAR, carried out in collaboration with the British Government Communications Headquarters (GCHQ). Operating from undisclosed interception points, the NSA and GCHQ copy entire data streams through fiber-optic cables connecting the data centers of major Silicon Valley corporations.
This becomes particularly perplexing when considering that, as revealed by a classified document acquired by The Washington Post in 2013, both the NSA and the FBI were already actively tapping into the central servers of nine prominent U.S. internet companies. This covert operation involved extracting audio and video chats, photographs, emails, documents, and connection logs, providing analysts with the means to monitor foreign targets. The method of extraction, as outlined in the document, involves direct collection from the servers of major U.S. service providers: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and Apple.
During the same period, the newspaper The Guardian reported that GCHQ -- the British counterpart to the NSA -- was clandestinely gathering intelligence from these internet companies through a collaborative effort with the NSA. According to documents obtained by The Guardian, the PRISM program seemingly allows GCHQ to bypass the formal legal procedures required in Britain to request personal materials such as emails, photos, and videos, from internet companies based outside the country.
PRISM emerged in 2007 as a successor to President George W. Bush's secret program of warrantless domestic surveillance, following revelations from the news media, lawsuits, and interventions by the Foreign Intelligence Surveillance Court. Congress responded with the Protect America Act in 2007 and the FISA Amendments Act of 2008, providing legal immunity to private companies cooperating voluntarily with U.S. intelligence collection. Microsoft became PRISM's inaugural partner, marking the beginning of years of extensive data collection beneath the surface of a heated national discourse on surveillance and privacy.
In a June 2013 statement, then-Director of National Intelligence James R. Clapper said "information collected under this program is among the most important and valuable foreign intelligence information we collect, and is used to protect our nation from a wide variety of threats. The unauthorized disclosure of information about this important and entirely legal program is reprehensible and risks important protections for the security of Americans".
So why the need for collection directly from fiber optic cables if these private companies themselves are already providing data to the national intelligence community? Upon further inquiry into the aforementioned data brokers to the NSA and CIA, it would appear that a vast majority of the new submarine fiber optic cables -- essential infrastructure to the actualization of the internet as a global data market -- are being built out by these same private companies. These inconspicuous cables weave across the global ocean floor, transporting 95-99% of international data through bundles of fiber-optic strands scarcely thicker than a standard garden hose. In total, the active network comprises over 1,100,000 kilometers of submarine cables.
Traditionally, these cables have been owned by a consortium of private companies, primarily telecom providers. However, a notable shift has emerged. In 2016, a significant surge in submarine cable development began, and notably, this time, the purchasers are content providers -- particularly the data brokers Meta/Facebook, Google, Microsoft, and Amazon. Of note is Google, having acquired over 100,000 kilometers of submarine cables. With the completion of the Curie Cable in 2019, Google's ownership of submarine cables globally stands at 1.4%, as measured by length. When factoring in cables with shared ownership, Google's overall share increases to approximately 8.5%. Facebook is shortly behind with 92,000 kilometers, with Amazon at 30,000, and Microsoft with around 6,500 kilometers from the partially owned MAREA cable.
There is a notable revival in the undersea cable sector, primarily fueled by investments from Facebook and Google, accounting for around 80% of 2018-2020 investments in transatlantic connections -- a significant increase from the less than 20% they accounted for in the preceding three years through 2017, as reported by TeleGeography. This wave of digital giants has fundamentally transformed the dynamics of the industry. Unlike traditional practices where phone companies established dedicated ventures for cable construction, often connecting England to the U.S. for voice calls and limited data traffic, these internet companies now wield considerable influence. They can dictate the cable landing locations, strategically placing them near their data centers, and have the flexibility to modify the line structures -- typically costing around $200 million for a transatlantic link -- without waiting for partner approvals. These technology behemoths aim to capitalize on the increasing demand for rapid data transfers essential for various applications, including streaming movies, social messaging, and even telemedicine.
The last time we saw such an explosion of activity in building out essential internet infrastructure was during the dot-com boom of the 1990s, in which phone companies spent over $20 billion to install fiber-optic lines beneath the oceans, immediately before the massive proliferation of personal computers, home internet modems, and peer-to-peer data networks.
The birthing of new compression technologies in the form of digital media formats itself would not have given rise to the panopticon we currently operate under without the ability to obfuscate mass uploading and downloading of this newly created data via the ISP rails of both public and private sector infrastructure companies. There is likely no accident that the creation of these tools, networks, and algorithms were created under the influence of national intelligence agencies right before the turn of the millennium, the rise of broadband internet, and the sweeping unconstitutional spying on citizens made legal via the Patriot Act in the aftermath of the events on September 11, 2001.
Only 15 years old, Sean Parker, the eventual founder of Napster and first president of Facebook -- a former DARPA project titled LifeLog -- caught the gaze of the FBI for his hacking exploits, ending in state-appointed community service. One year later, Parker was recruited by the CIA after winning a Virginia state computer science fair by developing an early internet crawling application. Instead of continuing his studies, he interned for a D.C. startup, FreeLoader, and eventually UUNet, an internet service provider. "I wasn't going to school," Parker told Forbes. "I was technically in a co-op program but in truth was just going to work." Parker made nearly six figures his senior year of high school, eventually starting the peer-to-peer music-sharing site that became Napster in 1999. While working on Napster, Parker met investor Ron Conway, who has backed every Parker product since, having also previously backed PayPal, Google, and Twitter, among others. Napster has been credited as one of the fastest-growing businesses of all time, and its influence on information goods and data markets in the internet age cannot be overstated.
In a study conducted between April 2000 and November 2001 by Sandvine titled "Peer-to-peer File Sharing: The Impact of File Sharing on Service Provider Networks", network measurements revealed a notable shift in bandwidth consumption patterns due to the launch of new peer-to-peer tooling, as well as new compression algorithms such as .MP3. Specifically, the percentage of network bandwidth attributed to Napster traffic saw an increase from 23% to 30%, whereas web-related traffic experienced a slight decrease from 20% to 19%. By 2002, observations indicated that file-sharing traffic was consuming a substantial portion, up to 60%, of internet service providers' bandwidth. The creation of new information good markets comes downstream of new technological capabilities, with implications on the scope and scale of current data stream proliferation, clearly noticeable within the domination of internet user activity belonging to peer-to-peer network communications.
Of course, peer-to-peer technology did not cease to advance after Napster, and the invention of "swarms", a style of downloading and uploading essential to the development of Bram Cohen's BitTorrent, were invented for eDonkey2000 by Jed McCaleb -- the eventual founder of Mt.Gox, Ripple Labs, and the Stellar Foundation. The proliferation of advanced packet exchange over the internet has led to entirely new types of information good markets, essentially boiling down to three main axioms; public and permanent data, selectively private data, and coveted but difficult-to-obtain data.

While publishing directly to Bitcoin is hardly a new phenomenon, the popularization of Ord -- released by Bitcoin developer Casey Rodarmor in 2022 -- has led to a massive increase in interest and activity in Bitcoin-native publishing. While certainly some of this can be attributed to a newly formed artistic culture siphoning away activity and value from Ethereum -- and other alternative businesses making erroneous claims of blockchain-native publishing -- the majority of this volume comes downstream from the construction of these inscription transactions that use the SegWit discount via specially authored Taproot script, and the awareness of the immutability, durability, and availability of data offered solely by the Bitcoin blockchain. The SegWit discount was specifically created to incentivize the consolidation of unspent transaction outputs and limit the creation of excessive change in the UTXO set, but as for its implications on Bitcoin-native publishing, it has essentially created a substantial 75% markdown on the cost of bits within a block that are stuffed with arbitrary data within an inscription. This is far from a non-factor in the creation of a sustainable information goods market.
Taking this one step further, the implementation of a self-referential inscription mechanism allows users to string data publishing across multiple Bitcoin blocks, limiting the costs from fitting a file into a single block auction. This implies both the ability to inscribe files beyond 4 MB, as well as the utility to reference previously inscribed material, such as executable software, code for generative art, or the image assets themselves. In the case of the recent Project Spartacus, recursive inscriptions that use what is known as a parent inscription were used in order to allow essentially a crowdfunding mechanism in order to publicly source the satoshis needed to publish the Afghan War logs onto the Bitcoin blockchain forever. This solves for the need of public and permanent publishing of known and available data by a pseudonymous set of users, but requires certain data availability during the minting process itself, which opens the door to centralized pressure points and potential censoring of inscription transactions within a public mint by nefarious mining pools.
With the advent of Bitcoin-native inscriptions, the possibility of immutable, durable, and censorship-reduced publishing has come to fruition. The current iteration of inscription technology allows for users to post their data via a permanent but publicly propagated Bitcoin transaction. However, this reality has led to yet-to-be confirmed inscription transactions and their associated data being noticed while within the mempool itself. This issue can be mitigated by introducing encryption within the inscription process, leaving encrypted but otherwise innocuous data to be propagated by Bitcoin nodes and eventually published by Bitcoin miners, but with no ability to be censored due to content. This also removes the ability for inscriptions meant for speculation to be front-run by malicious collectors who pull inscription data from the mempool and rebroadcast it at an increased fee rate in order to be confirmed sooner.
Precursive inscriptions aim to create the private, encrypted publishing of data spread out over multiple Bitcoin blocks that can be published at a whim via a recursive publishing transaction containing the private key to decrypt the previously inscribed data. For instance, a collective of whistleblowers could discreetly upload data to the Bitcoin blockchain, unbeknownst to miners or node runners, while deferring its publication until a preferred moment. Since the data will be encrypted during its initial inscribing phase, and since the data will be seemingly uncorrelated until it is recursively associated by the publishing transaction, a user can continually resign and propagate the time-locked parent inscription for extended durations of time. If the user cannot sign a further time-locked publishing transaction due to incarceration, the propagated publishing transaction will be confirmed after the time-lock period ends, thus giving the publisher a dead man's switch mechanism.
The specially authored precursive inscription process presented in this article offers a novel approach to secure and censorship-resistant data publishing within the Bitcoin blockchain. By leveraging the inherent characteristics of the Bitcoin network, such as its decentralized and immutable nature, the method described here addresses several key challenges in the field of information goods, data inscription, and dissemination. The primary objective of precursive inscriptions is to enhance the security and privacy of data stored on the Bitcoin blockchain, while also mitigating the risk of premature disclosure. One of the most significant advantages of this approach is its ability to ensure that the content remains concealed until the user decides to reveal it. This process not only provides data security but also maintains data integrity and permanence within the Bitcoin blockchain.
This leads us to the third and final fork of the information good data markets needed for the modern age; setting the price for wanted but currently unobtained bits.
ReQuest aims to create a novel data market allowing users to issue bounties for coveted data, seeking the secure and immutable storage of specific information on the Bitcoin blockchain. The primary bounty serves a dual role by covering publishing costs and rewarding those who successfully fulfill the request. Additionally, the protocol allows for the increase of bounties through contributions from other users, increasing the chances of successful fulfillment. Following an inscription submission, users who initiated the bounty can participate in a social validation process to verify the accuracy of the inscribed data.
Implementing this concept involves a combination of social vetting to ensure data accuracy, evaluating contributions to the bounty, and adhering to specific contractual parameters measured in byte size. The bounty fulfillment process requires eligible fulfillers to submit their inscription transaction hash or a live magnet link for consideration. In cases where the desired data is available but not natively published on Bitcoin -- or widely known but currently unavailable, such as a renowned .STL file or a software client update -- the protocol offers an alternative method to social consensus for fulfillment, involving hashing the file and verifying the resulting SHA-256 output, which provides a foolproof means of meeting the bounty's requirements. The collaborative nature of these bounties, coupled with their ability to encompass various data types, ensures that ReQuest's model can effectively address a broad spectrum of information needs in the market.
For ReQuest bounties involving large file sizes unsuitable for direct inscription on the Bitcoin blockchain, an alternative architecture known as Durabit has been proposed, in which a BitTorrent magnet link is inscribed and its seeding is maintained through a Bitcoin-native, time-locked incentive structure.
Durabit aims to incentivize durable, large data distribution in the information age. Through time-locked Bitcoin transactions and the use of magnet links published directly within Bitcoin blocks, Durabit encourages active long-term seeding while even helping to offset initial operational costs. As the bounty escalates, it becomes increasingly attractive for users to participate, creating a self-sustaining incentive structure for content distribution. The Durabit protocol escalates the bounty payouts to provide a sustained incentive for data seeding. This is done not by increasing rewards in satoshi terms, but rather by increasing the epoch length between payouts exponentially, leveraging the assumed long-term price increase due to deflationary economic policy in order to keep initial distribution costs low. Durabit has the potential to architect a specific type of information goods market via monetized file sharing and further integrate Bitcoin into the decades-long, peer-to-peer revolution.
These novel information good markets actualized by new Bitcon-native tooling can potentially reframe the fight for publishing, finding, and upholding data as the public square continues to erode.
The information war is fought on two fronts; the architecture that incentivizes durable and immutable public data publishing, and the disincentivization of the large-scale gathering of personal data -- often sold back to us in the form of specialized commercial content or surveilled by intelligence to aid in targeted propaganda, psychological operations, and the restriction of dissident narratives and publishers. The conveniences offered by walled garden apps and the private-sector-in-name-only networks are presented in order to access troves of metadata from real users. While user metrics can be inflated, the data gleaned from these bots are completely useless to data harvesting commercial applications such as Language Learning Models (LLMs) and current applicable AI interfaces.
There are two axioms in which these algorithms necessitate verifiable data; the authenticity of the model's code itself, and the selected input it inevitably parses. As for the protocol itself, in order to ensure replicability of desired features and mitigate any harmful adversarial functionality, techniques such as hashing previously audited code upon publishing state updates could be utilized. Dealing with the input of these LLMs' learning fodder is seemingly also two-pronged; cryptographic sovereignty over that data which is actually valuable to the open market, and the active jamming of signal fidelity with data-chaff. It is perhaps not realistic to expect your everyday person to run noise-generating APIs that constantly feed the farmed, public datasets with heaps of lossy data, causing a data-driven feedback on these self-learning algorithms. But by creating alternative data structures and markets, built to the qualities of the specific "information good", we can perhaps incentivize -- at least subsidize -- the perceived economic cost of everyday people giving up their convenience. The trend of deflation of publishing costs via digital and the interconnectivity of the internet has made it all the more essential for everyday people to at least take back control of their own metadata.
It is not simply data that is the new commodity of the digital age, but your data: where you have been, what you have purchased, who you talk to, and the many manipulated whys that can be triangulated from the aforementioned wheres, whats, and whos. By mitigating the access to this data via obfuscation methods such as using VPNs, transacting with private payment tools, and choosing hardware powered by certain open source software, users can meaningfully increase the cost needed for data harvesting by the intelligence community and its private sector compatriots. The information age requires engaged participants, incentivized by the structures upholding and distributing the world's data -- their data -- on the last remaining alcoves of the public square, as well as encouraged and active retention of our own information.
Most of the time, a random, large number represented in bits is of little value to a prospective buyer. And yet Bitcoin's store-of-value property is derived entirely from users being able to publicly and immutably publish a signature to the blockchain, possible only from the successful keeping of a private key secret. A baselayer Bitcoin transaction fee is priced not by the amount of value transferred, but by how many bytes of space is required in a specific block to articulate all its spend restrictions, represented in sat/vbyte. Bitcoin is a database that manages to incentivize users replicating its ledger, communicating its state updates, and utilizing large swaths of energy to randomize its consensus model.
Every ten minutes, on average, another 4 MB auction.
If you want information to be free, give it a free market.
This article is featured in Bitcoin Magazine's "The Inscription Issue". Click here to get your Annual Bitcoin Magazine Subscription.
Click here to download a PDF of this article.
For the past decade, the abbreviations AML and KYC have become an inextricable part of our lives. To help law enforcement track illegal funds, an increasingly constraining set of anti-money-laundering measures is being implemented across the globe. For the past two decades, it has involved extensive know-your-customer obligations for financial institutions, forced to check their clients' identities, backgrounds, and the nature of their activities. This system, based on surveillance and the presumption of guilt, has helped the global financial system to efficiently fight criminals by cutting off their money flows.
Or has it really?
Real-life numbers tell a different story. Several independent studies have found that AML and KYC policies enable the authorities to recover less than 0.1% of criminal funds. AML efforts cost a hundred times these amounts, but more importantly, they start to threaten our basic right to privacy.
The instances of absurd demands, like the one of a French man asked to justify the origin of €0.66 he wanted to deposit, are hardly raising any eyebrows anymore. Regulators face this ridicule without blinking, all while journalists and whistleblowers continue to expose billions of dollars laundered at the highest levels of the same institutions that put their regular clients through a bureaucratic nightmare.
This suggests that sacrificing our right to privacy may not be justified by the results.
The blockchain emerging as a free value-transferring system, as opposed to the KYC-gated fiat, has given hope to many personal freedom advocates. However, the regulators' response was to try and integrate both the acts of buying and transferring crypto into the current AML processes.
Does it mean that the blockchain has been tamed, with both the entrance and the exit sealed by the AML regulation?
Luckily, not yet. Or at least, not in every jurisdiction. For example, Switzerland, famous for its practical common sense, often allows companies to define their own risk exposure. This means that people can buy reasonable amounts of crypto without KYC.
The Swiss example could prove valuable in stopping global AML practices from spiralling out of control and bringing a surveillance state upon the world that used to be known as "free". It is worth taking a closer look at, but first, let's see why the traditional AML approach is failing.
Few people dare to question the effectiveness of the current AML-KYC policies: no one wants to appear on the "criminal" side of the debate. However, this debate is worth having, for our societies appear to be spending an indecent amount of money and effort on something that just does not work as intended.
As noted by the director of Europol Rob Wainwright in 2018: "The banks are spending $20 billion a year to run the compliance regime ... and we are seizing 1 percent of criminal assets every year in Europe."
This thought was developed in one of the most comprehensive studies on the effectiveness of AML, published in 2020 by Ronald Pol from La Trobe University of Melbourne. It found that "the anti-money laundering policy intervention has less than 0.1 percent impact on criminal finances, compliance costs exceed recovered criminal funds more than a hundred times over, and banks, taxpayers and ordinary citizens are penalized more than criminal enterprises." Furthermore, "blaming banks for not "properly" implementing anti-money laundering laws is a convenient fiction. Fundamental problems may lie instead with the design of the core policy prescription itself."
The study uses numerous sources from major countries and agencies, but its author admits it is nearly impossible to reconcile it all. Indeed, as strange as it may seem, despite billions of dollars and euros spent on AML, there is no generalized practice that could allow us to measure its effectiveness.
The reality, however, is difficult to ignore. Despite the 20 years of modern KYC practices, organized crime and drug use continue to rise. What's more, a number of high-profile investigations have shown massive money laundering schemes happening at the very top of respected financial institutions. Crédit Suisse helping Bulgarian drug dealers, Wells Fargo (Wachovia) laundering money for the Mexican cartels, BNP Paribas facilitating operations of a Gabonese dictator... This is not to mention tax frauds initiated by the banks themselves: Danske Bank, Deutsche Bank, HSBC, and so many others have been proven guilty of scamming their countries. Yet, the regulators' response was to tighten the rules surrounding small retail-sized transfers and create extensive red tape for average law-abiding citizens.
Why would they choose such cumbersome and inefficient measures? Perhaps the main reason here is that the organizations that define the rules are not responsible for either implementing them or for the end result. This lack of accountability could explain the increasingly absurd rules forcing financial institutions to maintain armies of compliance specialists, and regular people to jump through hoops to perform basic financial operations.
This reality is not simply frustrating; in a broader historical and political context, it reveals worrisome trends. The increasingly intrusive regulations have set up a framework allowing to efficiently filter people. This means that under the pretext of fighting terrorism, different groups can be cut off from the financial system. This includes politically exposed people, dissenting voices, homeless, non-conformists... or those involved in the crypto space.
The blockchain represents a major challenge for the fiat system because of its decentralized nature. Unlike centralized banks burdened with countless AML-related verifications, blockchain nodes simply run user-agnostic code.
There's no way a blockchain like Bitcoin could be shaped into the AML mold, however, the intermediaries, also known as VASP (virtual asset service providers), can be. Their AML duties now include two major categories: buying crypto and transferring crypto.
Transferring crypto falls under the prerogative of FATF, and most countries tend to implement this organization's recommendations sooner or later. These recommendations include the "travel rule", which implies that the data about the funds must "travel" together with them. Currently, FATF recommends that any fiat transfer over $1000 must be accompanied by the information on the sender and the beneficiary.
Different countries impose different thresholds for the travel rule, with $3,000 in the US, €1,000 in Germany, and €0 in France and Switzerland. The upcoming TFR regulation update will impose the mandatory KYC for every crypto transfer starting from €0 in all EU countries.
The good thing about blockchain, though, is that it does not need intermediaries for transferring value. However, it needs them for buying crypto with fiat.
The framework for buying crypto is determined by financial regulators and central banks, and this is where the countries' traditions play an important role. In France, a highly centralized country, an array of minute regulations, on-site inspections, and conferences define market practices in great detail. Switzerland, a decentralized country famous for its direct democracy based on consensus, typically grants financial intermediaries a certain autonomy in managing their own risk appetite.
Switzerland is also the country where one of the most prominent liberal economists Friedrich Hayek founded the famous Mont Pelerin Society. Even back in 1947, its members were worried about dangers to individual liberty, noting that "Even that most precious possession of Western Man, freedom of thought and expression, is threatened by the spread of creeds which, claiming the privilege of tolerance when in the position of a minority, seek only to establish a position of power in which they can suppress and obliterate all views but their own."
Interestingly, a company called Mt Pelerin is operating today on the banks of the Geneva Lake, and this company is a crypto broker.
Switzerland is far from the libertarian tax haven that many believe it is. It has succumbed to international pressure by de facto canceling its centuries-old banking secrecy tradition for foreign residents. Now, it is a member of the OECD treaty on the automatic exchange of information, and the zeal with which it applies FATF recommendations shows the willingness to shake off its previously sulfurous image. Indeed, FINMA decided to implement the travel rule for crypto starting from 0€, including for unhosted wallets, as early as 2017. In contrast, the "conservative" European Union will enforce this obligation only in 2024.
However, when the funds don't explicitly leave the country, Switzerland still prefers to not micromanage its financial institutions and does not impose tons of paperwork for routine operations. It now stands as one of the rare countries on the old continent where people can buy crypto without being profiled. This means that companies like Mt Pelerin can process retail-size crypto transactions of CHF 1,000 per day without requiring the client to verify their identity.
This does not mean an open bar, but rather a higher degree of autonomy. For example, Mt Pelerin implements its own fraud detection methods and reserves the right to refuse transactions that raise suspicion. In contrast to the heavily bureaucratic procedures that other countries impose, this approach actually boasts a high success rate at filtering out fraudulent transaction attempts. After all, the firms operating on the front lines often have a better understanding of the ever-evolving fraud tactics than government officials.
For the sake of our societies, the Swiss approach to AML must be preserved and replicated. In a time when mass surveillance has become routine, and the CBDC development threatens to impose total control over our personal finances, we are closer than ever to the dystopia that Friedrich Hayek feared so much.
By controlling our day-to-day transactions, any government, even the best-intentioned, could manipulate our lives and effectively "obliterate any views but their own". That's why we buy Bitcoin, and that's why we want to do so without KYC.
What about the criminals, you might ask? Shouldn't we cut off their access to money to curb their interest in underground entrepreneurship?
Admittedly, after 20 years of modern AML, this thesis has proven itself wrong. So why not accept the fact that criminals enter our money flows and just follow that money to expose their operations? Continue reading Part 2 to learn more.
A special thank you to Biba Homsy, the Regulatory & Crypto Lawyer at Homsy Legal, and the team of Mt Pelerin for sharing their insights.
This is a guest post by Marie Poteriaieva. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
LQWD Technologies Corp., an infrastructure and liquidity provider for the Bitcoin Lightning Network, has announced a new partnership with Amboss Technologies Inc. to become their premiere Lightning Network Liquidity Service Provider (LSP), according to a press release sent to Bitcoin Magazine. As part of the partnership, LQWD will contribute an initial 10 Bitcoin in liquidity to Amboss, with plans to deploy more Bitcoin throughout the collaboration.
"Partnering with LQWD ensures that Amboss's global customers have direct access to institutional-grade liquidity for Bitcoin payments, allowing LQWD to generate additional yield through their nodes on the Lightning Network," said Amboss Co-Founder and CEO Jesse Shrader. "Additionally, this partnership increases the supply side of Amboss's liquidity marketplace, enabling LQWD to fulfill the market demand for Lightning Network liquidity."
Amboss Technologies specializes in data analytics solutions tailored for the Bitcoin Lightning Network and provides products like Magma and Hydro for market organization and liquidity automation. Magma serves as a liquidity marketplace, while Hydro enables advanced liquidity automation for seamless Lightning Network payments.
"This partnership enables LQWD to deploy more of our company-owned Bitcoin while potentially capturing significant transaction volume and generating yield on our Bitcoin holdings," stated Shone Anstey, Chief Executive Officer of LQWD. "Importantly, we maintain full sovereignty and custody throughout the process. This strategic alliance signifies a significant step forward for both LQWD and Amboss, as we work together to enhance liquidity and efficiency within the Bitcoin Lightning Network ecosystem."
The Lightning Network (LN) has witnessed significant growth, with LN activity increasing by 1,200% over the past two years, according to the release. This surge in adoption, coupled with the integration of stable coin transaction capability, opens up LN to a wider user base and attracts forward-thinking businesses and Bitcoin exchanges looking for faster and cheaper payment solutions compared to traditional rails like Visa and Mastercard.
If you want to hold a large amount of bitcoin securely, it makes sense to investigate how the wealthiest bitcoin holders handle this task. While wealth doesn't cause infallibility, these entities have the most to lose from making a mistake. They should be highly motivated to put substantial thought and research into the security of their bitcoin.
Identifying the wealthiest bitcoin holders can be difficult, and asking them to reveal the full details of their security is unlikely to be successful. However, the bitcoin blockchain provides us with some valuable information. The transaction history and balances of all bitcoin addresses is publicly-available knowledge.
If an entity (person or group) owns a lot of bitcoin, it's possible that they keep their bitcoin spread across many different addresses, each with a smaller-sized balance. Those addresses wouldn't necessarily stand out from the crowd. In some cases, it's impossible to associate different addresses with the same wallet or owner. In other cases, association between addresses requires blockchain analysis, often relying on advanced techniques and assumptions which are not guaranteed to provide accurate information.
Although it's challenging to definitively identify the wealthiest entities in terms of bitcoin, and precisely how much bitcoin they own, it's trivial to identify the wealthiest bitcoin addresses. There are a few websites that track these addresses in real time. The nature of these addresses can provide a lot of clues about how the bitcoin is secured.
For example, if you are familiar with address types, you'll know that any address that begins with a "1" is a P2PKH address, and therefore must be a singlesig arrangement. Similarly, any address that begins with "bc1q" and has a length of 42 characters is a P2WPKH address, and must also be a singlesig address. Bitcoin held by one of these address types isn't utilizing multisig protection. Using SSS or MPC would be the only way to achieve institutional-grade security, as discussed in our article covering thresholds.
Meanwhile, any address that begins with a "3" is a P2SH address. Any address that begins with "bc1q" and has a length of 62 characters is a P2WSH address. These address types have the possibility of utilizing multisig. However, only after bitcoin has been spent out of these addresses will the custody structure be revealed. Some P2SH addresses are actually singlesig, a structure that was temporarily popular while SegWit was being initially adopted. Therefore, if one of these address types has never been spent out of, the custody structure is unknown.

Let's take a look at the 81 addresses which each hold more than 10,000 bitcoin, as of January 30, 2024. Altogether, these addresses hold more than 2.5 million bitcoin.
Bitcoin Balance | Address | Custody Structure |
248,597 | 34xp4vRoCGJym3xR7yCVPFHoCNxv4Twseo | Singlesig |
204,010 | bc1qgdjqv0av3q56jvd82tkdjpy7gdp9ut8tlqmgrpmv24sq90ecnvqqjwvw97 | 3-of-5 Multisig |
127,136 | bc1ql49ydapnjafl5t2cp9zqpjwe6pdgmxy98859v2 | Singlesig |
115,177 | 39884E3j6KZj82FK4vcCrkUvWYL5MQaS3v | Unknown |
94,643 | bc1qazcm763858nkj2dj986etajv6wquslv8uxwczt | Singlesig |
94,505 | 37XuVSEpWW4trkfmvWzegTHQt7BdktSKUs | Singlesig |
79,957* | 1FeexV6bAHb8ybZjqQMjJrcCrHGW9sb6uF | Singlesig** |
73,393 | 3M219KR5vEneNb47ewrPfWyb5jQ2DjxRP6 | Singlesig |
69,370 | bc1qa5wkgaew2dkv56kfvj49j0av5nml45x9ek9hz6 | Singlesig |
68,200 | 3LYJfcfHPXYJreMsASk2jkn69LWEYKzexb | Singlesig |
66,465 | bc1qjasf9z3h7w3jspkhtgatgpyvvzgpa2wwd2lr0eh5tx44reyn2k7sfc27a4 | 3-of-5 Multisig |
59,300 | bc1qd4ysezhmypwty5dnw7c8nqy5h5nxg0xqsvaefd0qn5kq32vwnwqqgv4rzr | 3-of-5 Multisig |
53,880 | 1LdRcdxfbSnmCYYNdeYpUnztiYzVfBEQeC | Singlesig** |
51,830 | 1AC4fMwgY8j9onSbXEWeH6Zan8QGMSdmtA | Singlesig |
44,000 | 1LruNZjwamWJXThX2Y8C2d47QqhAkkc5os | Singlesig |
43,602 | 1Ay8vMC7R1UbyCCZRVULMV7iQpHSAbguJP | Singlesig |
41,334 | 3LCGsSmfr24demGvriN4e3ft8wEcDuHFqh | 2-of-2 Multisig |
37,932 | bc1qs5vdqkusz4v7qac8ynx0vt9jrekwuupx2fl5udp9jql3sr03z3gsr2mf0f | 3-of-6 Multisig |
37,927 | 3LQUu4v9z6KNch71j7kbj8GPeAGUo1FW6a | Unknown |
36,000 | bc1q7ydrtdn8z62xhslqyqtyt38mm4e2c4h3mxjkug | Singlesig |
32,321 | 12XqeqZRVkBDgmPLVY4ZC6Y4ruUUEug8Fx | Singlesig |
32,019 | 3MgEAFWu1HKSnZ5ZsC8qf61ZW18xrP5pgd | 2-of-3 Multisig |
31,643 | bc1qx9t2l3pyny2spqpqlye8svce70nppwtaxwdrp4 | Singlesig |
31,379 | bc1qjh0akslml59uuczddqu0y4p3vj64hg5mc94c40 | Singlesig |
31,275 | 3FHNBLobJnbCTFTVakh5TXmEneyf5PT61B | Unknown |
31,000* | 12ib7dApVFvg82TXKycWBNpN8kFyiAN1dr | Singlesig** |
30,175 | bc1qf2yvj48mzkj7uf8lc2a9sa7w983qe256l5c8fs | Singlesig |
28,151* | 12tkqA9xSoowkzoERHMWNKsTey55YEBqkv | Singlesig** |
26,140 | 1aXzEKiDJKzkPxTZy9zGc3y1nCDwDPub2 | Singlesig** |
24,606 | 19N9sDbJ7MDQcPFSjPNqjNDzyRNbNsQ6Zv | Singlesig |
24,495 | 17MWdxfjPYP2PYhdy885QtihfbW181r1rn | Singlesig |
24,067 | 38UmuUqPCrFmQo4khkomQwZ4VbY2nZMJ67 | 2-of-6 Multisig |
23,969 | 19D5J8c59P2bAkWKvxSYw8scD3KUNWoZ1C | Singlesig |
23,922 | 3G98jSULfhrES1J9HKfZdDjXx1sTNvHkhN | 3-of-8 Multisig |
23,789 | 1m5SViB9XNwsusvnnUqpfL9Q1E5EZxPHs | Singlesig |
22,514 | 15cHRgVrGKz7qp2JL2N5mkB2MCFGLcnHxv | Singlesig |
22,221 | bc1qr4dl5wa7kl8yu792dceg9z5knl2gkn220lk7a9 | Singlesig |
20,544 | bc1qm34lsc65zpw79lxes69zkqmk6ee3ewf0j77s3h | Singlesig |
20,008 | 17rm2dvb439dZqyMe2d4D6AQJSgg6yeNRn | Singlesig |
19,852 | 39gUvGynQ7Re3i15G3J2gp9DEB9LnLFPMN | Singlesig |
19,679 | 3EMVdMehEq5SFipQ5UfbsfMsH223sSz9A9 | 4-of-8 Multisig |
19,414* | 1PeizMg76Cf96nUQrYg8xuoZWLQozU5zGW | Singlesig** |
18,500 | bc1qkz55x35wlnrkrn5n0nq4wwsme9vszrwavu5qf4 | Singlesig |
18,320 | bc1qlhpkdeaaa345c4dw90hmvm3nn2r32f9jdj2v2p | Singlesig |
17,969 | bc1qtrxc0use4hlm7fl0j6t37z7qlwl5eppj8lywz6 | Singlesig |
17,945 | bc1qhk0ghcywv0mlmcmz408sdaxudxuk9tvng9xx8g | Singlesig |
17,928 | bc1qcdqj2smprre85c78d942wx5tauw5n7uw92r7wr | Singlesig |
16,858 | bc1q5vwscmf85w2vlq0qvr33dgpvu5rlrd42cqw6qn | Singlesig |
16,610 | 3FupZp77ySr7jwoLYEJ9mwzJpvoNBXsBnE | 2-of-3 Multisig |
16,453 | bc1qx2x5cqhymfcnjtg902ky6u5t5htmt7fvqztdsm028hkrvxcl4t2sjtpd9l | 2-of-2 Multisig |
16,348 | 34HpHYiyQwg69gFmCq2BGHjF1DZnZnBeBP | Unknown |
16,307 | 1BAuq7Vho2CEkVkUxbfU26LhwQjbCmWQkD | Singlesig |
16,227 | 1N4WQbt63gnThPwHFZ1w9adEnE1xB8ctXk | Singlesig |
16,231 | bc1qchctnvmdva5z9vrpxkkxck64v7nmzdtyxsrq64 | Singlesig |
16,224 | 1932eKraQ3Ad9MeNBHb14WFQbNrLaKeEpT | Singlesig |
15,900 | 32TiohXoCmHr87xVm3E9A3sLiWBJjYn1gf | 4-of-6 Multisig |
15,746 | 3JZq4atUahhuA9rLhXLMhhTo133J9rF97j | Singlesig |
15,392 | 1GR9qNz7zgtaW5HwwVpEJWMnGWhsbsieCG | Singlesig |
15,251 | 1KDWnWQNSGZZ8QHcKPgzz3DGRkmgVv9HhJ | Singlesig |
14,676 | bc1qvhxafz8dqk8c25jsx669yd6qrxhl5dx72dyryp | Singlesig |
14,599 | 35pgGeez3ou6ofrpjt8T7bvC9t6RrUK4p6 | 2-of-3 Multisig |
14,000 | 1BZaYtmXka1y3Byi2yvXCDG92Tjz7ecwYj | Singlesig |
13,805 | 3NpXph8WN1U9hwXjg1bRtzTff1tPR2Gpw4 | Unknown |
13,003 | bc1q4vxn43l44h30nkluqfxd9eckf45vr2awz38lwa | Singlesig |
12,891 | 1KVpuCfhftkzJ67ZUegaMuaYey7qni7pPj | Singlesig |
12,858 | 1CiAnTJn6eHTU89PeihdMhT7KcQZxVZ4fy | Singlesig |
12,840 | 3BMEXqGpG4FxBA1KWhRFufXfSTRgzfDBhJ | 3-of-4 Multisig |
12,803 | 3HfD4pvF43jdu9dzVMEr1b8AnDHooRGc5t | 3-of-9 Multisig |
12,795 | 1DNUjpHPNKMoKYBHxJz2Sh1uQQdJkGsXj5 | Singlesig |
12,267 | 1PJiGp2yDLvUgqeBsuZVCBADArNsk6XEiw | Singlesig |
11,985 | 1CKVszDdUp4ymGceAZpGzYEFr4RPNHYqaM | Singlesig |
11,673 | 3A9qNS69dngSU2ak8BwZKEExeVnL2RqpYJ | Unknown |
11,400 | 1Cr7EjvS8C7gfarREHCvFhd9gT3r46pfLb | Singlesig |
11,115 | bc1qgrvchamnmmaancn3vwea6elnvexpylzh30rhjz | Singlesig |
10,840 | bc1qk7fy6qumtdkjy765ujxqxe0my55ake0zefa2dmt6sjx2sr098d8qf26ufn | 3-of-5 Multisig |
10,771* | 1F34duy2eeMz5mSrvFepVzy7Y1rBsnAyWC | Singlesig** |
10,500 | bc1qhd0r5kh3u9mhac7de58qd2rdfx4kkv84kpx302 | Singlesig |
10,486 | bc1q93njc4we4s088a2nz6c9e6vthc5h4ake53rxmd | Singlesig |
10,217 | 1Q8QR5k32hexiMQnRgkJ6fmmjn5fMWhdv9 | Singlesig |
10,009* | 1f1miYFQWTzdLiCBxtHHnNiW7WAWPUccr | Singlesig** |
10,002 | bc1qsxdxm0exqdsmnl9ejrz250xqxrxpxkgf5nhhtq | Singlesig |
*Likely lost
**Not using MPC
Out of these 81 addresses, at least six of them are holding bitcoin that is likely to be lost (179,302 BTC). These six addresses were created by their owners in 2010 or 2011, when bitcoin had a much smaller value and was not taken as seriously as it is today. Five of the six have never been spent from, and the other one made its last withdrawal in July of 2010.
The remaining 75 addresses use a variety of custody structures. Let's break it down:
Address Type | Addresses (%) | Total Bitcoin Balance (%) |
Singlesig | 53 (70.7%) | 1,745,905 (67.6%) |
Multisig | 16 (21.3%) | 608,773 (23.6%) |
Unknown | 6 (8.0%) | 226,205 (8.8%) |
As explained in our article discussing institutional-grade threshold security, it's likely that the 53 singlesig addresses are using either SSS or MPC. Two of the addresses, however, are unlikely to be using MPC, because they were created before 2018, when the first-ever MPC threshold protocols for ECDSA were invented. It's possible that these addresses are using SSS instead.
The 16 addresses that we know are using multisig have all been spent out of, and in doing so they have revealed their specific quorum structure. There is a wide assortment of quorums:
The 2-of-2 quorums stand out as the only quorums in the list which don't offer inherent protection from single points of failure. While a distributed 2-of-2 multisig can protect against theft, it requires other methods to protect against loss (such as each key using distributed SSS or MPC shares). You can read more about how different quorums protect from theft and loss to varying degrees, in our broader multisig article.

After looking at the data, at least one thing is clear. Among the owners of the wealthiest bitcoin addresses--some of whom include the biggest cryptocurrency exchanges and even the U.S. Department of Justice--there is no consensus on the best method to secure bitcoin.
Some of these entities use multisig addresses, with typical quorums like 2-of-3 and 3-of-5, but there are several unusual quorums as well. Many entities use singlesig addresses, which could be utilizing SSS or MPC. The details surrounding SSS or MPC threshold quorums are never publicly recorded on the blockchain, limiting the extent of this investigation. It's possible that some of these singlesig addresses are not employing any threshold security at all, which would mean that certain stashes of bitcoin currently worth more than $400M are notably under-secured.
As we covered in a recent article, multisig always has a higher security ceiling than singlesig. When a singlesig address is used (as is the case with at least 70% of the addresses holding more than 10,000 BTC) there is a missed opportunity for additional security. While singlesig does provide some benefits for spending convenience and transaction fees, one might expect these benefits to be less important than security, for an entity holding bitcoin worth millions or billions of dollars.
The truth behind why singlesig addresses are so commonly found at the top levels is unclear. It may amount to a lack of education, or a historical lack of products and services leveraging the combination of SSS and MPC alongside multisig. Luckily, Unchained has pioneered a simple path to access these combinations, unlocking the highest levels of security obtainable. For private wealth and enterprise clients, we offer a vault product built with a foundation of multisig, and keys that can be spread amongst institutional key agents. Each of these key agents can deploy their own threshold security using SSS or MPC. Book a free consultation!
Originally published on Unchained.com.
Unchained Capital is the official US Collaborative Custody partner of Bitcoin Magazine and an integral sponsor of related content published through Bitcoin Magazine. For more information on services offered, custody products, and the relationship between Unchained and Bitcoin Magazine, please visit our website.
Today, the Human Rights Foundation (HRF) announced its most recent round of Bitcoin Development Fund grants, according to a press release sent to Bitcoin Magazine.
$500,000 is being granted across 14 different projects around the world focusing on global education, Lightning Network development, decentralized communications, and providing nonprofits and human rights groups with an easier onramp to "financial freedom tools," per the release. The main areas of focus for these grants center around Latin America, Asia, and Africa.
This announcement comes only a few months after their last round of grants in December, also donating $500,000 to worldwide Bitcoin projects. While the HRF did not disclose exactly how much money each project is receiving, the following 14 projects are the recipients of today's round of grants worth $500,000 in total:
USD E-Cash for Bitcoin by Calle, a USD-based Chaumian e-cash system built on the Cashu protocol. This system aims to enable private, affordable, and stable use of USD-denominated credits, all interoperable with the broader Bitcoin Lightning network. USD E-Cash is positioned as an alternative to major stablecoins, in that it does not have any connection to the traditional banking system. The core idea is that activists anywhere can exchange their bitcoin for privacy-protecting dollar-denominated E-Cash, with the trade-off of being custodial. Funding will support the full development of this project.
BTCPay Server, a free, open-source, self-hosted payment solution that enables individuals and businesses to accept Bitcoin payments. BTCPay provides a platform for merchants in difficult political and economic climates to process global payments, manage crowdfunding campaigns, and offers developers opportunities to kickstart their projects on top of Bitcoin. Funding for BTCPay Server will support UI/UX improvements, feature enhancements, contributor rewards, and training programs.
BOB Builders Residency Program, an in-person residency for Free and Open-Source Software (FOSS) developers located in Thailand. The new cohort of developers will focus on "Toolings to Reinforce Bitcoin's Decentralization," to combat centralizing forces in the software ecosystem. The previous cohort, also supported by HRF, focused on privacy. Funds will be used to support the residents of this second cohort, covering living and travel expenses.
Yibaochina.com 议报中文, a popular news platform led by Citizen Power Initiatives for China, serves Chinese scholars, intellects, and writers abroad. Dedicated to promoting democracy, human rights, and the rule of law in the global Chinese-speaking community, Yibao has gained a significant readership, particularly in pro-democracy communities within China. HRF's grant will support the wages of writers, editors, and translators of the site, as well as social media promotion efforts, as they translate Bitcoin educational materials and news items into Chinese for wide circulation into the world's biggest dictatorship.
Bitcoin Innovation Hub, a physical space and community center promoting the socioeconomic transformation of refugees, asylum seekers, and other vulnerable communities led by Noble Nyangoma in Kampala, Uganda. The hub offers a range of vocational training and financial literacy to women and men in various fields, where they learn how to use and how to earn Bitcoin, regardless of what kind of ID they hold. Funding will support the addition of vocational classes (ie. digital skills, carpentry, and baking) for thousands of students in the East African region, enabling stateless communities to earn Bitcoin for their work.
BITCOIN DADA, a non-profit initiative founded by Kenyan entrepreneur Lorraine Marcel, aims to empower African women through financial education. BITCOIN DADA provides a safe space for women to learn about Bitcoin as a tool for financial freedom and build up their skill set. Funds will support the expansion across Africa, the creation of multilingual educational resources, and promote women-led businesses adopting Bitcoin. The grants in this round to Bitcoin DADA and to the Bitcoin Innovation Hub are generously supported by Strike's nonprofit initiative.
The Bitcoin Design Foundation, which supports the Bitcoin Design Community, is dedicated to providing design infrastructure and resources to bitcoin designers and developers, including those building for people living under authoritarian regimes and in developing economies. The funding will support the development of the Bitcoin UI Kit (a resource that help people learn, design, prototype, and build full bitcoin applications) as well as the addition of new and emerging techniques for privacy and self-sovereignty in the Bitcoin Design Guide. Improving the UX of Bitcoin wallets remains one of its top goals.
Bitcoin Op-Tech, a technical Bitcoin newsletter renowned for its industry-leading resources, technologies, and techniques tailored for Bitcoin developers, businesses, and organizations. The newsletter regularly covers issues of privacy, censorship-resistance, and decentralization which are core to HRF's mission. Additionally, Bitcoin Op-Tech offers workshops, documentation, original research, and case studies. Funds will be allocated towards operational expenses and growth strategies.
Damus Android, a communications application using the nostr protocol. Developed by Will Casarin, Damus ensures free speech online -- critical for people living in difficult political environments without being censored -- and enables users to receive Bitcoin through its "zapping" functionality. Funding will be used to develop the Damus application for Android devices, helping to potentially onboard millions of new users in authoritarian countries and the developing world.
Bitcoin Core Developer Pablo Martin, whose initial work addressed a vulnerability that caused a Bitcoin node to crash and shut down. Martin continues to contribute, review, and put forth proposals advancing Bitcoin, including the http-rest interface, bitcoin-cli, p2p, rpc, and the wallet within the Bitcoin repository, while also contributing to Bitcoin Core GUI repositories. Funds will support his ongoing contributions to Bitcoin development, the likes of which are crucial to keeping Bitcoin a secure tool for activists everywhere.
LNbits, a multi-user and account system for the Lightning Network, enables users to create separate Lightning wallets for friends and family. Built by software developer Ben Arc, LNbits aims to decentralize custodianship and provides users with a robust suite of Bitcoin tools they can run for themselves, for others, or as part of a stack. Funding will support the core contributors' salaries, bounties, and educational outreach efforts through workshops and video tutorials.
Bitcoin Policy Summit 2024, a one-day conference bringing together policymakers, academics, and industry leaders to explore the opportunities and challenges of Bitcoin. The event aims to reshape the narrative surrounding Bitcoin, advocate for its benefits in liberal democracies, and highlight its potential to undermine closed societies. Funding will support event logistics, speaker travel, and attendance by human rights advocates.
Bitcoin for Billions, a series of informative videos created by Bitcoin educator, Paco de la India. The videos, initially available in four regional languages -- Hindi, Bengali, Marathi, and Gujarati -- aim to have a wide audience among the 750 million people in India who speak these languages. Topics include the concept of bitcoin as freedom money and practical guidance on purchasing and self-custodying bitcoin safely, items which are increasingly important under a regime that continues to trend more authoritarian. The grant will be used for research, content creation, translation, and promotion of the videos.
Scalar School, founded by Luciana Ferreira, a Brazil-based Bitcoin and Lightning development program dedicated to training early-stage Bitcoin developers. The school equips students with a comprehensive understanding of Bitcoin development, philosophy, and community engagement, preparing them for future opportunities in esteemed programs such as Chaincode Labs. The grant will go towards teachers' salaries, training workshops, and university outreach and will give a boost towards developers living in South America.
The Human Rights Foundation (HRF) is a nonpartisan, nonprofit 501(c)(3) organization that promotes and protects human rights globally, with a focus on closed societies. The HRF continues to raise support for the Bitcoin Development Fund, and applications for support can be submitted here.
As the value of your bitcoin grows, so does your need for secure key storage. One such solution is a hardware wallet, a physical device that allows you to securely hold the keys to your bitcoin. But hardware wallets aren't the only option for storing your bitcoin keys--there are also software wallets, paper wallets, and even "brain wallets." So why specifically choose a hardware wallet?

Hardware wallets enable you to generate and hold the keys to your bitcoin entirely offline, known as cold storage. This stands in contrast to hot wallets, which are more susceptible to remote attacks such as malware and SIM swap attacks (still more secure than a custodian or an exchange!).
You can think of this as similar to building a ship in a bottle. Your wallet's seed, which is used to generate the keys to your bitcoin, is generated inside the device and cannot be digitally exported. At no point do the keys ever leave the device. Even if a hardware wallet is connected to a virus-infected computer (which is not recommended), the keys would still be protected, often in a secure element.
When you want to move your bitcoin, you author a transaction using wallet software, send it to the hardware wallet, sign it on the hardware wallet itself using your private keys, and then send it back to the internet-connected wallet software for it to be broadcast to the bitcoin network.

If someone were to gain physical access to your hardware wallet, there are unique features hardware wallets offer that help you defend against attacks. Some of these security features include a secure element, firmware verification, and PINs for first-layer defense.
A secure element is a microprocessor used to isolate, store, and protect sensitive data. In a hardware wallet, a secure element provides a higher level of protection against physical compromise compared to the standard environment on a mobile phone, desktop, or laptop. For example, this makes it more difficult to compromise your device via fault attacks, side-channel attacks, and cold boot attacks.
Firmware verification is a way to verify the validity of a hardware wallet's onboard software. This protects against counterfeit versions and supply-chain attacks. Verifying the firmware ensures the use of a genuine, unaltered version of the hardware. Wallet software from manufacturers like Trezor, Ledger, and others verify the device firmware every time you connect them to your PC.
Access PINs in many hardware wallets help prevent anyone but the owner from getting immediate access to the ability to sign with the keys stored on the device. In most cases, the penalty for failing to properly enter the PIN over a certain number of tries is an increasing delay between incorrect guesses. With some hardware wallets, exceeding the number of allowable PIN guesses can result in a factory reset of the device or even render it permanently unusable.
A duress PIN is a security feature that can help protect your bitcoin in the event of a $5 wrench attack. Duress PINs are particularly important for hardware wallets (due to them being used to secure larger amounts of bitcoin), and the available functionality is particularly robust in some cases.
For example, the Coldcard hardware wallet offers three types of duress PINs: one that unlocks a decoy wallet, one that destroys the seed upon entry, and one that creates a countdown to customizable "brick modes". If you end up in a duress scenario, these tools offer you confidence that attackers won't be able to access your primary bitcoin keys--if any at all.

It's possible to store your keys offline with a laptop or desktop and secure them from physical attacks. However, the general-purpose architectures of these devices present a larger attack surface for skilled attackers. This means there are more ways for attackers to exploit software, firmware, and hardware to engineer ways to steal your private keys.
In contrast, hardware wallets are built with specialized hardware that simplifies their functionality to very specific tasks and limits their connectivity to the internet and other devices. Even with a secure element to keep key data behind a firewall, some hardware wallets restrict the way they physically connect with external devices--air-gapped hardware wallets primarily interface with other devices via microSD card. Many manufacturers also offer bitcoin-only firmware to further simplify functionality.
Hardware wallets may be more limited in functionality and convenience than general purposes devices, but that limited functionality also means limited vulnerability. This also has the side benefit of creating less risk for new holes to be discovered that manufacturers must plug with firmware updates or hardware revisions.


You may think you don't own enough bitcoin for it to be worth the effort to buy a hardware wallet and learn how to securely hold your keys offline. One reason to get a hardware wallet now is to prepare for bitcoin's upward price swings.
It's common bitcoin wisdom to treat your holdings as if they're worth 10x what they are today--historically, a move like this can come quickly and unexpectedly. Additionally, if your bitcoin holdings would be uncomfortably large for standard singlesig self-custody at a 10x value increase, it may be time to consider a more secure self-custody model such as multisig.

Because bitcoin transactions are irreversible, it's important to be certain when you send bitcoin that it goes to the correct address. This is important for both sending bitcoin to someone else and sending bitcoin to a wallet controlled by the keys on the hardware wallet(s) you own.
With software wallets, malware could replace a real address with an attacker's address in the UI, making it difficult to verify its authenticity. There's also "clipper" malware, which switches the receiving address in your computer's clipboard, and other attack vectors.
Hardware wallets help with this by including a physical screen that displays the address you want to send funds to, allowing you to verify it prior to spending. As long as your device hasn't been physically compromised, you can be confident that the address you're shown is controlled by the keys stored offline on the device. If you're sending funds to a remote recipient, it's best to confirm the address you're sending to through multiple channels.

All bitcoin wallets depend on entropy--randomness--to generate seeds, and seeds are the master secret that generates your bitcoin private keys. Entropy can be generated in many ways, from basic on-device random number generators, to long strings of random text entry, to dice rolls or playing cards.
Dice rolls are widely considered one of the best ways to generate your own entropy, minimizing the involvement of third-parties in generating the randomness needed to initialize a bitcoin wallet. Some hardware wallets, such as Coldcard, allow you to enter dice rolls on-device to generate a seed phrase. You can press 1-6 for each roll and it will use the rolls to generate your seed.
While you don't need a hardware wallet to generate your own entropy (you could do so on a permanently offline laptop, for example), hardware wallets uniquely allow you to do so in a way that's convenient and secure. Generating your own entropy in the physical world can be fun and a great learning exercise, but it's pointless without the right environment to help you preserve the marginal security you may obtain by doing so.

Traveling with small amounts of bitcoin can be easily done with a mobile phone or another less secure device, but larger amounts of bitcoin require more forethought. Traveling with keys on a laptop computer or mobile device is risky because these devices are usually hot (internet-connected), have more limited physical protections, and have larger attack surfaces.
Hardware wallets offer convenience and security if you need to keep one or more bitcoin keys on your person while traveling.
You don't have to worry about sketchy WiFi connections or USB ports, you can use duress features as described above if someone were to physically attack you, and you're more protected if your device becomes lost, stolen, or confiscated (attackers would have to do defeat the hardware wallet's purpose-built security). And they still offer convenient access if you need to spend.

Multisig wallets are built by combining multiple keys (versus singlesig wallets that use just one). Requiring more than one key to spend bitcoin adds security and redundancy to your wallet, making them useful for securing larger amounts of bitcoin.
The more secure the individual keys involved in constructing a multisig wallet are, the more secure the multisig wallet is itself. Hardware wallets enable you to conveniently build a multisig wallet with clearly delineated keys securely held offline. Like with singlesig, hardware wallets also let you verify multisig addresses offline when sending bitcoin.
Using multiple hardware wallets is a natural fit for multisig because multisig is often used for maximizing security and redundancy for large amounts of cold storage bitcoin, a goal which physical devices and seed phrase backups also help you to achieve.
The first step to upgrading your bitcoin security is always to take self-custody, whether hot or cold, to eliminate the risk involved with trusting custodians such as exchanges. From there, you can explore additional security tools, such as multisig, to find the right balance of security and accessibility for your circumstances.

Originally published on Unchained.com.
Unchained Capital is the official US Collaborative Custody partner of Bitcoin Magazine and an integral sponsor of related content published through Bitcoin Magazine. For more information on services offered, custody products, and the relationship between Unchained and Bitcoin Magazine, please visit our website.
Palladium and Botanix Labs have announced the launch of a new stablecoin, PUSD, on Bitcoin's first EVM-equivalent Layer 2 network, according to a press release sent to Bitcoin Magazine.
The PUSD stablecoin, developed by Palladium Labs, boasts a unique feature of being over-collateralized by 110%, a strategic measure aimed at enhancing its resilience against potential risks inherent in DeFi infrastructure. Importantly, the stablecoin's algorithmic monetary policy attempts to remain immune to governance changes or manipulation by administrator keys, aiming to ensure its integrity and reliability.
"To realize the true value of decentralized finance, crypto needs to break free from infrastructure that is susceptible to exploits and manipulation," stated Palladium Labs CEO Akash Gaurav. "At Palladium, we designed this stablecoin for resilience and reliability. By leveraging the unique capabilities of the Botanix EVM, we can radically increase the security and reliability of stablecoin access for millions of people using Bitcoin."
Operating on the Botanix EVM, which has been in development since early 2023, Palladium leverages the capabilities of this platform to enhance the security and accessibility of stablecoin transactions for Bitcoin users. The Botanix EVM's underlying sidechain protocol, known as the Spiderchain, plays a pivotal role in safeguarding funds transferred from the Bitcoin base layer to the EVM network.
"The importance of native stablecoins to the technological renaissance happening on Bitcoin cannot be overstated," said Willem Schroe, inventor of the Spiderchain and co-founder of Botanix Labs. "We are thrilled to support the Palladium team in launching their over-collateralized stablecoin on our EVM network."
With the launch of PUSD on Bitcoin's first EVM Layer 2 network, Palladium and Botanix Labs aim to meet the growing demand for secure and efficient DeFi solutions, seeking to pave the way for a new era of financial innovation on the Bitcoin blockchain.
Luxor Technology Corporation (Luxor) and Bitnomial, Inc. have announced the launch of the first US exchange-traded Hashrate Futures, according to a press release sent to Bitcoin Magazine. Set to debut on Bitnomial's derivatives exchange by the end of this month, these futures contracts are specifically tailored to cater to Bitcoin miners and institutional investors alike.
"Hashrate has one of the highest volatilities of major commodities, and the April 2024 Bitcoin Halving will exacerbate this volatility," said Luxor's Head of Derivatives, Matt Williams. "Bitcoin miners need additional methods to mitigate this price risk to ensure the longevity of their businesses. Exchange-traded hashrate futures will allow them to quickly move in and out of hedging positions to de-risk their revenue streams, and the revenue certainty should improve their credit profile with lenders, which will lower their cost of securing capital."
With the impending 2024 Bitcoin Halving in mind, the Hashrate Futures aim to provide miners with a tool to hedge their future revenue streams while offering investors access to a tradable derivative tracking Bitcoin mining hashrate. The contracts, denominated in 1 petahash (PH) units and with monthly durations, will reference Luxor's Bitcoin Hashprice Index for settlement, effectively tracking the value of the underlying commodity, i.e., hashrate.
Accessible to those with Futures Commission Merchant (FCM) accounts connected to the Bitnomial exchange, the Hashrate Futures is the latest addition to Luxor's suite of hashrate financial products.
"As we approach the Bitcoin halving and witness the unprecedented demand for spot Bitcoin ETFs surpassing the available mined supply, Bitnomial stands as a pivotal bridge in the crypto ecosystem." stated Bitnomial Founder and CEO, Luke Hoersten. "Our listed hashrate and physically delivered bitcoin futures and options empower miners to navigate this evolving landscape seamlessly. Through Bitnomial, miners can efficiently trade hashrate-bitcoin futures spreads, gaining invaluable bitcoin-denominated hashrate exposure while effectively hedging and delivering mined bitcoin directly to consumers via a federally regulated exchange. This convergence of innovation and regulation solidifies Bitnomial's commitment to fostering a robust and accessible marketplace for all participants in the crypto space."
As part of Bitnomial's Bitcoin Product Complex, these physically backed contracts intend to provide a unique opportunity for market participants, with growing interest evidenced by record-high volumes and open interest during Q4 of 2023.
Page created in 0.043 seconds with 13 queries.
